This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Tag: Security
-

How to Limit the Use of Personal Data by Others: A Guide for Privacy-Conscious Individuals
In today’s digital age, personal data is being collected by various organizations and entities, including social media platforms, e-commerce websites, and mobile apps.
-

Protecting Your Personal Information: Effective Cybersecurity Strategies for Individuals
In today’s digital age, cyber threats are becoming increasingly prevalent and sophisticated, making it essential for individuals to take proactive steps to protect their personal information from cyberattacks. This article I will discuss effective cybersecurity strategies that individuals can adopt to safeguard their personal data. Use Strong and Unique Passwords One of the simplest and…
-

Ten tips to prevent cyber attacks
Cyber attacks are on the increase for both private individuals and sensitive businesses with today’s seriously deteriorating world situation. The current situation leads to foreign powers increasing their need to obtain sensitive information about a country’s interests. Or something else that can affect the national security or that of activities that are necessary for the country…
-

5 Security Measures You Can Easily Implement on Your eCommerce Site
eCommerce has come a long way from a burgeoning industry to a massive global player in online business. As of 2021, there are approximately 24 million eCommerce sites across the world wide web. Unfortunately, eCommerce sites risk privacy invasion, data theft, and illegitimate copies like anything involving money and valuable data. But you needn’t worry.
-

5 Advantages of Digital Currencies
In 2008 the first digital currencies emerged in the form of Bitcoins. At first, it was a novelty and few really took it seriously. This was evident in its reception to the global economy. Although many people bought up the currency it still didn’t fare well in the markets and was considered volatile for several…
-

6 Ways an IT Service Provider Help Your Small Business
Productivity is essential in any small business and there are many different IT issues that can affect productivity, however, the one way to overcome all of these issues is to hire a managed IT services provider to look after your IT systems.
-

How to use HMAC with Postman to test webhooks
In this how-to, I will show how I implemented HMAC in a Cloud Function that acts as a webhook using the node Express application framework. The focus of this article is how I implemented HMAC and not on how to build a Cloud Function webhook.
-
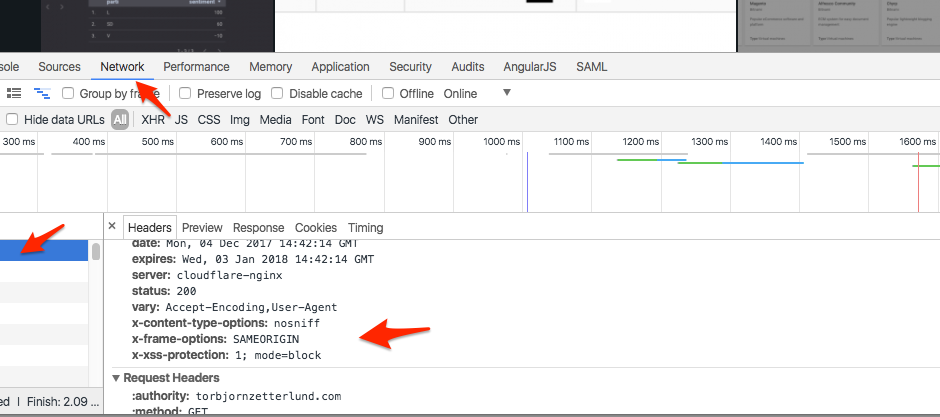
Hardening your HTTP response headers with .htaccess
HTTP Response headers are typically used to transfer security policies to the browser. Bypassing security policies back to the client, hosts can ensure a much safer browsing experience for their visitors and also reduce the risk for everyone involved.
-
The analysis of DDoS attacks
Are you interested in one of our biggest threat to the performances of our websites, I’m. One of the biggest threats is DDoS Attacks.
-

Do you have a password policy that is wrong
What if I say that everything IT does about passwords is wrong! It does not matter how secure you make a user’s password initially, the user will eventually choose their own password.

